In the context of computer networks, a port can refer to either a physical or a virtual connection point. A physical port allows a cable to connect with the computers, routers, modems, or any other peripheral devices. Virtual ports are part of TCP/IP networking.
Most of the software applications use these ports to connect and communicate with other devices for example an ssh client gets connected to the ssh server through port 22. Computers and routers automatically manage network traffic traveling via their virtual port.
A firewall, in a system additionally provides some control over the flow of traffic on each virtual host for security purposes.
How to identify a virtual port?
Virtual ports are identified for each protocol and address combination by 16-bit unsigned numbers and which is known as the port number. The range of these ports is from 0 to 65535. Some examples are –
PROTOCOLS PORT NUMBER FTP (data transfer) 20 FTP (command control) 21 SSH 22 TELNET 23 HTTP 80 HTTPS 443
Virtual ports are further classified in –
- 0 to 1023 – are well-known ports also known as system ports
- 1024 to 49151 – are registered ports also known as user ports
- 49152 to 65535 – are dynamic ports and also known as private ports
How to Scan a Port?
A network firewall controls the ports. These can be either closed or open. There may be some applications that are using the open port of your system. The practice of attempting to connect to a range of port in a sequence on a computer is known as port scanning. A port scanning is usually intended either for malicious cracking attempts or It is done by a network admin who is looking for possible vulnerability to prevent such attacks.
How to check for open ports in Linux?
There are various ways to check open ports in your system. You can use netstat, Nmap, SS command, and lsof, etc. These command-line utilities display ports along with some other useful information.
Port Scan Using netstat command
Execute the following command in your terminal-
sudo netstat -tpuln|grep LISTEN
Look at the output of the command in the below image-
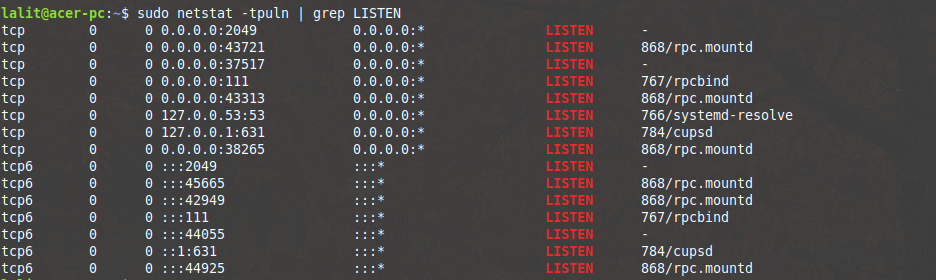
Where,
-t – Display only TCP connections
-u – Used to display only UDP connections
-l – this option used to display listening server socket
-p – Show the PID and name of the program
-n – Don’t resolve names
Port Scan using SS utility
This is another utility to investigate sockets. It uses options like netstat command-
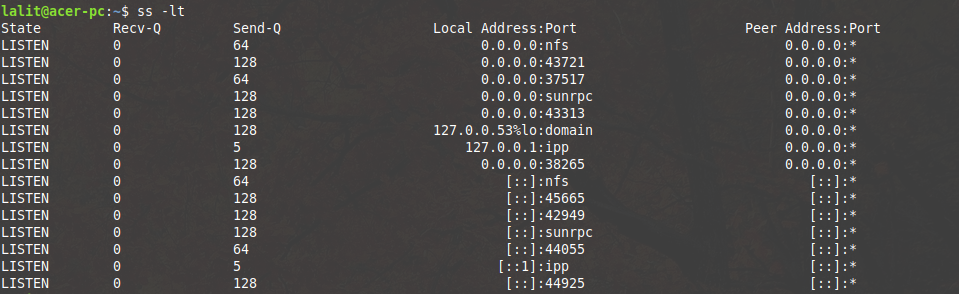
sudo ss -lt
This command will display the listening TCP connections. Look at the output of the command in the below image-
Port Scan Using lsof command
lsof command is used to list open files we can use it to check open TCP and UDP ports also –
sudo lsof -i -P -n
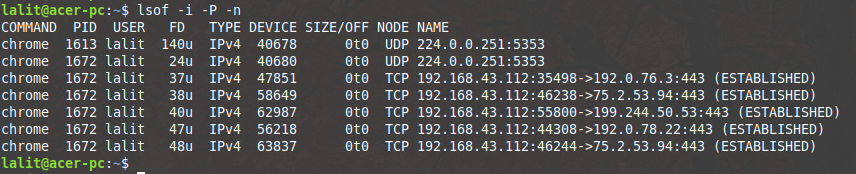
Where,
-i – Looks for listing ports
-P – Inhibit the conversion of port numbers to port names for network file
-n – Do not use DNS name
Port Scan Using Nmap command
Nmap doesn’t come pre-installed with some Linux distributions. So before start using Nmap for scanning ports you have to install it in your system. You can use the following command to install it-
sudo apt-get install nmap -y
The syntax of using Nmap command is –
nmap [scan_type] [options] <target_specification>
For example –
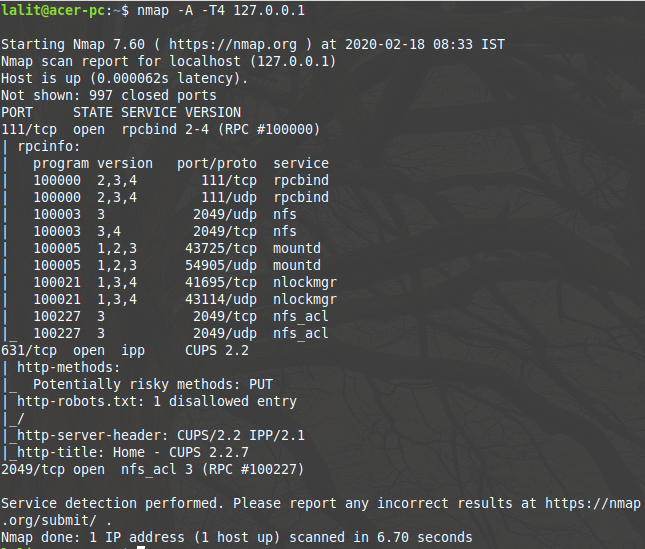
nmap -A -T4 127.0.0.1
Look at the output of the command in the below image-
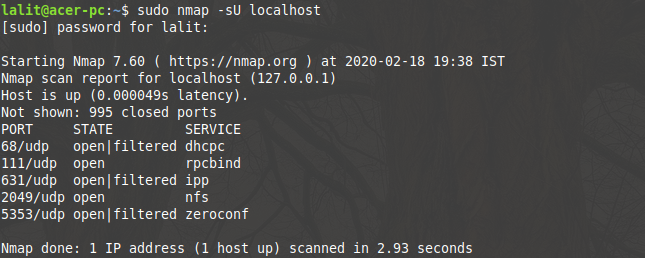
sudo nmap -sU localhost
Now see the output of this command in the below image-
You can see the detailed article on how to use Nmap to scan ports in Linux. Also, you can use Zenmap which is the official graphical interface of the Nmap security scanner.
