There are lots of network mapping and security auditing tools available for reviewing and analyzing a computer network for possible security vulnerabilities and loopholes. These tools can be used by a network administrator or a computer security professional to evaluate the possible threats in their system. Nmap is from one of these tools, we are going to discuss it in this article.
What is Nmap
Nmap (Network Mapper) is a free and open-source tool for network discovery and vulnerability scanning in a system connected to the Internet. It can determine information like hosts available on the network, service offered by those hosts, operating system that they are running, packet filters/firewalls they are using, etc. Nmap discovers this information by sending packets and analyzing the response on that network. Initially, it was released for Linux but later makes available for other major operating systems too.
How do we install it
To install Nmap in Debian based Linux distributions, execute the following command in the terminal
sudo apt-get install nmap -y
In RPM-based Linux distributions execute the following command in the terminal
sudo yum install nmap -y
Or you can download it from here.
GUI tool for Nmap
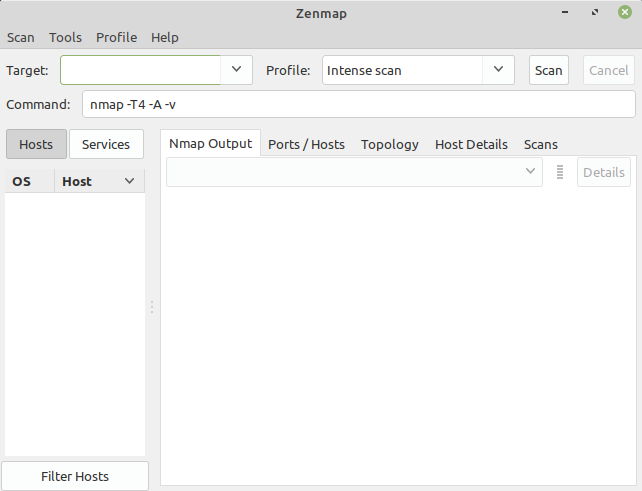
Zenmap is the official graphical user interface of the Nmap security scanner. It provides several options like scan results can be saved and viewed later, you can compare these saved scans to see how they differ, and also you can see the network topology maps. This application is available freely for multiple platforms. You can install Zenmap by using the following commands –
In Debian and similar distributions use –
sudo apt-get install zenmap -y
In RPM-based distributions use-
sudo yum install zenmap -y
Look at the snapshot below it shows the GUI of Nmap.
How to use Nmap for port scanning?
A beginner may find it easier to use Nmap in GUI while others can feel comfortable to use Nmap in their terminal. You can use either way for the security scan. The basic syntax of Nmap command is given below-
nmap [scan_type] [options] <target_specification>
For example –
nmap -A -T4 scanme.nmap.org
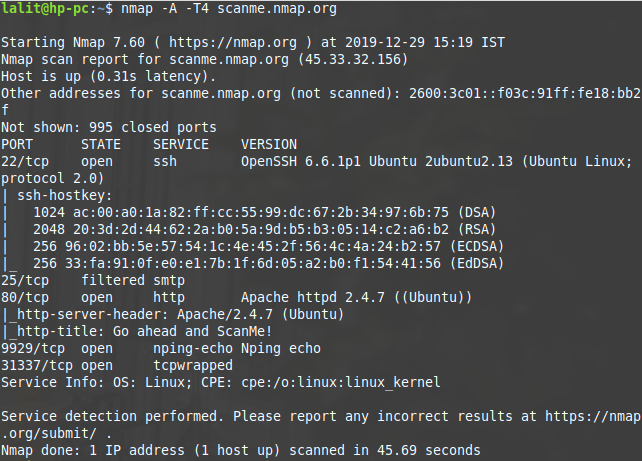
In this example-A is the option that is used to enable OS detection, version detection, script scanning, and traceroute.-T is the timing template, Nmap offers six timing templates these can be specified with numbers (0-5) or with names. The timing template names with corresponding numbers are –
0-paranoid
1-sneaky
2-polite
3-normal
4-aggressive
5-insane
Where 0 is used for a slow network scan, and it uses a serial scan method while 5 is used for an extremely fast network scan it uses parallel scanning strategies.
Execute the Nmap command without any argument in the terminal to see the available options that can be used while scanning a target. These options are used to optimize a scan. Scanning every port of every single IP address is slow and usually unnecessary. So anyone should use the right options to meet the exact results with reasonably fast speed.
Are there any legal Issues in using Nmap?
Nmap is a tool that can be used to discover security loopholes in a system connected to the Internet. If it is used properly it can help you to protect your network from hackers. But if used improperly, it can get you into trouble. Intentionally anyone can attempt to gain unauthorized access to a computer system, and if get accessed to the data of that system can be misused. Unauthorized port scanning is illegal in some jurisdictions. You should take a written authorization from the target network administrator before initiating a scan to avoid the legal issues.
If you are interested to know more about Nmap and its usage then you should follow the reference guide. If you have a query/suggestion related to this topic you can write to us in the comments below.