A firewall is a network security system that monitors incoming and outgoing network traffic flows through a system. It allows or blocks the data packets based on a set of security rules that are predefined in the system. It acts as a barrier between internal and external sources such as the internet and blocks malicious traffic.
FreeBSD provides three firewalls all of them are built-in into the base system-
- PF
- IPFW
- IPFILTER
Here in this article, we will discuss setting up a firewall with PF on FreeBSD 12.1.
PF (Packet Filter)
PF is the acronym for packet filter it was originally developed for OpenBSD but later ported for various other operating systems. It is a stateful firewall you can compare it with Netfilter (iptables), ipfw, or ipfilter used in Linux.
Enable the Packet filter
So before you start using the PF firewall first you need to turn it on. You can enable it by using the following command –
sysrc pf_enable=yes
Next, add the pf ruleset configuration file path to /etc/rc.conf file, use –
sysrc pf_rules=/etc/pf.conf
Turn on logging support for pf by using –
sysrc pflog_enable=yes
Now add the logging file path to /etc/rc.conf file –
sysrc pflog_logfile=/var/log/pflog
Now when next time you open your system it will start the PF firewall automatically.
Defining PF firewall rules
First, open the /etc/pf.conf file in your terminal by using the given command –
vi /etc/pf.conf
You can start adding rules into this file as given below –
block all
pass in proto tcp to port { 22 }
pass out proto { tcp udp } to port { 22 80 123 443 }The PF firewall reads this file from top to bottom. The first line will block all the incoming and outgoing traffic on the system. In the next line, rules will be revised initially it was blocking all the traffic but now it allows the incoming traffic for ssh that means you will now able to ssh into a server.
In the last line, the outbound traffic is allowed for services such as SSH, HTTP, NTP, and HTTPS, etc. which means now you can do tasks like downloading the packages from the internet, synchronizing system time, etc.
You can create a set skip rule for the loopback devices because it does not need to filter the traffic. Internet control message protocol(ICMP) is required for tools used for debugging and troubleshooting of TCP/IP network so we also define a rule for ICMP. Now simply you can copy and paste the given lines into the /etc/pf.conf file.
#skip loopback interface
set skip on lo
#block all the traffic in and out on the system
block all
#allow incoming traffic to port ssh
pass in proto tcp to port { 22 }
#allow outbound traffic for ssh, HTTP, NTP, HTTPS
pass out proto { tcp udp } to port { 22 80 123 443 }
pass inet proto icmp from any to anyAt the end of this file, you can append any new rule as given above. Once you are done with adding rules save the file and exit from the editor.
Start the PF firewall
Start the PF firewall services by using –
service pf start
Use the given command to start logging support –
service pflog start
Check for errors in /etc/pf.conf
After modifying the pf.conf files check for any errors by executing one of the given commands –
service pf check
or
pfctl -n -f /etc/pf.conf
Check pf status
Now to check the status of pf you can use the following command in the terminal –
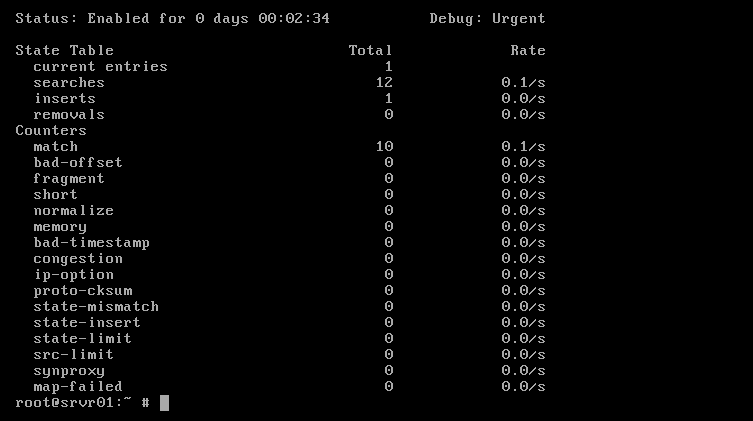
service pf status
Now see the output first thing is it confirms that our firewall is working and secondly the criteria of the ruleset are matched 10 times.
Enable or disable PF from the command line
Use the following command to disable the PF from the terminal –
pfctl -d
Or if you want to enable PF firewall use –
pfctl -e
We can advance the rules by using macros and tables. You can learn more about defining rules and using pfctl command from PF (Packet Filter) FreeBSD.